Beware of this Wire Transfer Scam
Revolution Group has recently seen an increase in a highly successful spearphishing scheme. Attackers are disguising their operation with internal email domains to request wire transfers from an executive in the organization. The scammers are targeting finance departments and resources within an organization that have the ability to make the payment requests. Spammers are also registering domains with similar characteristics as the target domain. Many victims fail to notice the slight difference in the domain, and believe the email came from a trusted sender.
Through social engineering, procurement and research on social media, attackers are able to identify key financial decision makers within an organization to target. The scammers will then send the fake wire transfer requests from an executive.
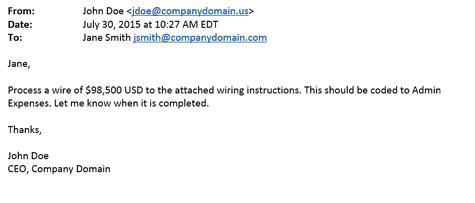
Below is a sample of a common email thread used to target an organization:
How to Protect Yourself from a Wire Transfer Attack
All companies are vulnerable to an attack, especially mid-large companies that frequently make large wire transfers. It’s important to stay vigilant and follow internal protocols in order to prevent an attack from taking place. Here are five ways to protect your organization:
Review wire transfer protocols with internal resources
Every organization should have protocols in place to ensure all wire transfers requests are not fraudulent attacks. These sophisticated attacks are tailored to look like they’re coming from a C-level executives, and often times they can route responses back to them without the C-level executive knowing. It is important to verify with decision-makers either in person or on the phone before transfers are made.
Set strict protocols with your bank to ensure verification methods are completed
No matter how difficult it maybe for the bank to connect with the CEO or CFO to authorize a transfer, it is imperative they understand verbal confirmation is necessary before a wire transfer is processed.
There are examples where an attack took place while a C-level executive was traveling. When the bank called to verify the request, the attackers intercepted the voice mail message, and used an email to confirm they received the voice mail and successfully authorized the transfer.
Educate and train employees to recognize social engineering and phishing attacks
Often times, an attack is set into motion by gaining initial access to an email server through a successful phishing attempt. From there, spammers have access to internal information and email correspondence, which helps them execute a spearphishing campaign.
The only way to prevent these attacks is to remain vigilant and understand the different methods of phishing, social engineering and spearphishing.
In this previously recorded webinar, Revolution Group IT Architect Scott Coffman discusses how to reduce spam and phishing in your organization.
Check email headers to ensure they’re originating from the organization’s domain
One of the quickest ways to identify a fraudulent attempt within an organization is to look at the domain from the sender. Often times, spammers use a similar domain to disguise their attack. In the example above, an email came from a domain name similar to the organization’s domain; however, after looking closer, the recipient noticed a .US domain instead of a .com. This is the first sign that an attempt to fraudulently collect funds is being made.
Register domain names similar to your organization’s domain name
As we’ve mentioned, spammers disguise their fraud attempts with similar looking domain names. In order to prevent these spearphishing attacks, organizations can purchase all of the domain names that are similar.
What To Do if You’re Attacked
If an attacker successfully executes a spearphishing campaign, they will act quickly to empty the bank accounts. After this happens, it is nearly impossible to recover the financial losses from the bank. Victims of these fraudulent attacks will not have the support of the bank, as they followed all protocols you set in place. It is important to act as quickly as possible in order to stop the transfer.
Immediately contact the bank
If you’re able to catch the mistake before the funds are cleared, it is possible to recall the request and freeze the fraudulent account. Contact the fraud department at the bank to inform them of the attack and have them put actions in place to prevent the account from being cleared.
Contact local and federal law enforcement
This is important for a variety of reasons, including insurance purposes.
As long as your organization remains vigilant in the cyber world, you can prevent these attacks. If you would like more information on how you can protect yourself in a cyber world, please call us at 614-212-1111.

